Have you ever wanted to watch someone reverse engineer a piece of hardware and pick up some tips? You can’t be there while [Jeremy] tears open a Netgear N300 router, but you can see his process step by step in some presentation charts, and you’ll get a few ideas for the next time you want to do something like this.
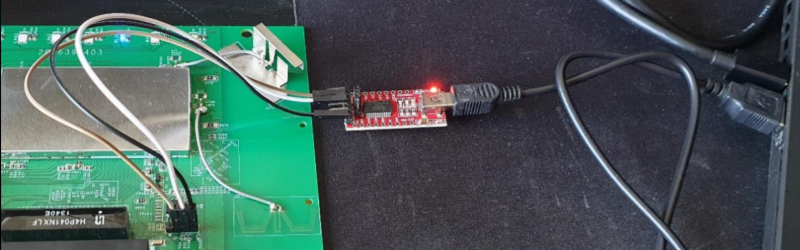
The first part of the presentation might be a little basic for most Hackaday readers, but presumably, the intended audience might not know much about soldering or multimeters. But we enjoyed the methodology used to work out the UART pins on the board. We would have read the baud rate with the scope, which [Jeremy] does, but he also mentions a script to work it out and create a minicom profile that looked interesting.
The router runs OpenWRT, so once you have access to the UART, you are in as root. Getting into the bootloader allowed access to the firmware. At first, [Jeremy] though he found a JTAG interface, but it didn’t work. He suspects the JTAG is disabled, but shows how he would dump the firmware from another device that does have JTAG. He also shows how you could dump the flash chip directly. Fair warning: it required removing the device from the PCB.
Once you have the firmware, there are tools to extract the root file system and even emulate the running system. Then you no longer have a hardware problem, you have a software problem, and that’s where [Jeremy] leaves it.
We were impressed with the completeness of the presentation and how each step provided multiple methods. Sometimes, as you can see, one method doesn’t work and you need to try an alternative.
You can hack other types of devices using similar techniques. Even games.

Recent Comments